AutoIt3 droppers with FileInstall + CallWindowProc: an IR playbook
SANS ISC documented fresh AutoIt3-compiled droppers that embed payloads with FileInstall, write obfuscated bytes to %TEMP%, allocate RWX memory with VirtualAlloc, then execute shellcode via CallWindowProc. The samples include commodity payloads (e.g., Quasar RAT, Phantom stealer). DFIR teams should assume more of these will show up in email/download chains and prepare hunts and triage checklists now (SANS ISC diary). (isc.sans.edu)
Intrusion Flow
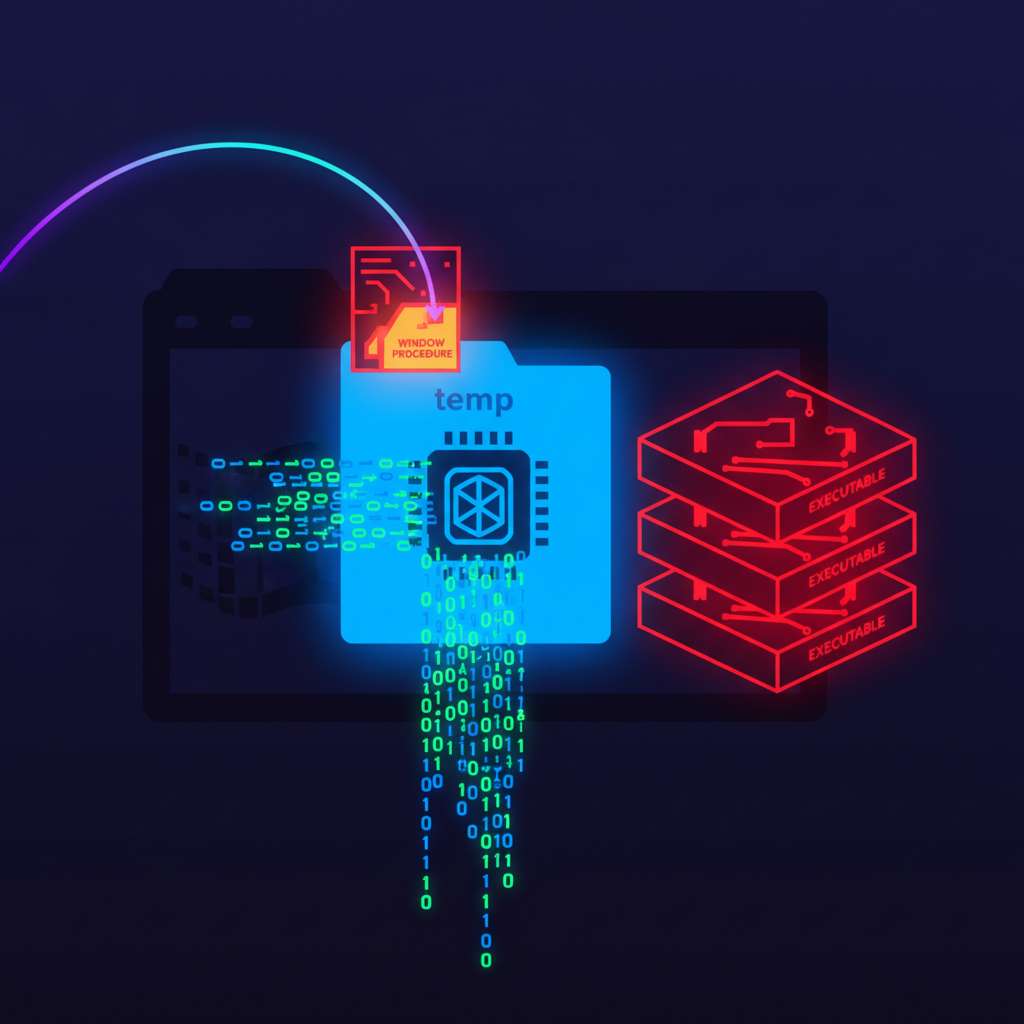
- Delivery: compiled AutoIt3 PE executable. AutoIt’s compiler bundles the tokenized script and any files added via FileInstall into the binary, enabling single-file distribution (AutoIt compiler docs). (autoitscript.com)
- Drop/Stage: the script calls FileInstall to extract embedded files at runtime; in the analyzed sample, it wrote artifacts like “inhumation” and “buncal” into %TEMP% (FileInstall reference; SANS ISC diary). (autoitscript.com)
- Decode: simple string arithmetic deobfuscates API names and payload bytes (e.g., shift by −1 per character), yielding resolved imports such as kernel32/user32 and shellcode buffers (SANS ISC diary). (isc.sans.edu)
- Load: the script allocates memory with VirtualAlloc using MEM_COMMIT | MEM_RESERVE (0x3000) and PAGE_EXECUTE_READWRITE (0x40), then copies the shellcode into the buffer (VirtualAlloc documentation). (learn.microsoft.com)
- Execute: CallWindowProc is invoked with a pointer into the shellcode, executing on the current GUI thread without creating a new thread-behavior that can blend in with benign GUI activity (CallWindowProc documentation; prior SANS note on this technique). (learn.microsoft.com)
Key Artifacts to Pull
- Disk
- %TEMP% artifacts named by the script (e.g., embedded files like “inhumation”, “buncal”) and the original AutoIt3-compiled loader executable. Parse MFT/USN timestamps and look for same-second write/execute patterns (SANS ISC diary). (isc.sans.edu)
- Prefetch for the loader EXE to confirm first/last run, run count, and child DLLs. PECmd supports all modern Prefetch formats (PECmd). (github.com)
- Program execution artifacts: Amcache.hve commonly records executed PE metadata including path and SHA-1; use it to corroborate execution of the loader (Amcache background and path). (cybertriage.com)
- Memory
- Dump live memory if possible. Look for RWX regions and injected code; Volatility’s malfind helps surface suspicious VADs with PAGE_EXECUTE permissions (Volatility malfind). (github.com)
- Logs/Telem
- Sysmon Event ID 1 (process creation) for the loader and its child processes; Event ID 11 (FileCreate) for new files in %TEMP%. Enable network (ID 3) if applicable. Confirm Sysmon schema and event semantics in Microsoft’s reference (Sysmon docs). (learn.microsoft.com)
Detection Notes
- Static triage
- AutoIt compiled loaders can often be identified by tooling and YARA. Community YARA rules flag AutoIt-compiled PEs; the ecosystem reports broad sightings of such rules in the wild (MalwareBazaar YARA: AutoIT_Compiled). (bazaar.abuse.ch)
- Indicators in extracted content: look for tokens/FileInstall references, kernel32/user32 API usage via DllCall, and strings like VirtualAlloc/CallWindowProc after deobfuscation. Extraction/decompilation helpers exist, e.g., AutoIt-Ripper and myAut2Exe (use in a lab VM) (AutoIt-Ripper; myAut2Exe). (github.com)
- Behavior hunts (host)
- Group signals: short-lived loader that (a) creates extensionless temp files, (b) immediately reads them, (c) spawns no obvious child interpreters, and (d) exhibits GUI-thread API usage. Correlate Sysmon ID 1 + 11 with the loader image path and %TEMP% targets (Sysmon docs). (learn.microsoft.com)
- Behavioral rationale
- CallWindowProc is a legitimate GUI API that can invoke an arbitrary function pointer; adversaries use it to execute payloads without CreateThread, which can sidestep common thread-creation detections (CallWindowProc; SANS technique overview). (learn.microsoft.com)
Response Guidance
- Triage and containment
- If the loader executed, isolate the endpoint, capture memory, and acquire a full disk image or triage package including %TEMP%, user profile AppData, Prefetch, Amcache.hve, and relevant Event Logs/Sysmon. Prioritize memory due to ephemeral RWX buffers (Volatility malfind). (github.com)
- Analysis workflow
- Identify the loader: check signature and entropy; run Detect-It-Easy or similar to fingerprint the packer/interpreter; scan with AutoIt-specific YARA (Detect-It-Easy project page; YARA AutoIT_Compiled). (github.com)
- Extract embedded resources: attempt AutoIt-Ripper/myAut2Exe; search for AU3 headers and exported resources; validate any decoded shellcode buffers before execution in a sandbox (AutoIt-Ripper; myAut2Exe). (github.com)
- Confirm behavior/lateral artifacts: correlate FileCreate in %TEMP% and subsequent memory execution; if payload families are indicated (e.g., Quasar/Phantom), pivot to family-specific hunts (SANS ISC diary discussion of payloads). (isc.sans.edu)
- Hardening and prevention
- Application control: allow-list legitimate AutoIt use; block unsigned AutoIt-compiled executables from user-writeable paths. Preferably, distribute approved .a3x/.exe only via trusted software channels (AutoIt compiler behavior and formats). (autoitscript.com)
- Telemetry: ensure Sysmon/EDR capture of process, file, and network activity; many detections for shellcode allocation hinge on correlating VirtualAlloc + immediate RWX execution with unusual temp-file stages (Sysmon overview; VirtualAlloc documentation). (learn.microsoft.com)
Takeaways
- Treat AutoIt3-compiled PEs that write to %TEMP% and then allocate RWX memory as high-priority investigations. Hunt for FileInstall use, temp-file stages, VirtualAlloc with RWX, and CallWindowProc execution. Instrument Sysmon, build YARA for AutoIt loaders, and keep an extraction/deobfuscation toolchain ready (SANS ISC diary; VirtualAlloc; CallWindowProc; AutoIt FileInstall). (isc.sans.edu)